Pell Center Panel Discussion Addresses Cybersecurity Workforce Management: Challenges & Solutions
 NEWPORT, RI—Over 50 senior leaders representing Rhode Island’s private and public sectors, law enforcement, and academia gathered at the Pell Center on March 10 to participate in a two-hour panel discussion entitled “Enterprise Cybersecurity Workforce Management.” The event, part of the ongoing Rhode Island Corporate Cybersecurity Initiative (RICCI), brought together cybersecurity experts and practitioners to discuss ways to optimize enterprise resources, prioritize essential security tasks, and develop a comprehensive cybersecurity strategy—one that integrates best practices across policy, technology, and people—to increase the security posture of organizations. The panel included Francesca Spidalieri, Pell Center Senior Fellow for Cyber Leadership; Maurice Uenuma, Senior Vice President at Center for Internet Security; Geoff Hancock, CEO for the Advanced Cybersecurity Group; and Jack Nicholas, Director and General Counsel at Creative Services Inc.
NEWPORT, RI—Over 50 senior leaders representing Rhode Island’s private and public sectors, law enforcement, and academia gathered at the Pell Center on March 10 to participate in a two-hour panel discussion entitled “Enterprise Cybersecurity Workforce Management.” The event, part of the ongoing Rhode Island Corporate Cybersecurity Initiative (RICCI), brought together cybersecurity experts and practitioners to discuss ways to optimize enterprise resources, prioritize essential security tasks, and develop a comprehensive cybersecurity strategy—one that integrates best practices across policy, technology, and people—to increase the security posture of organizations. The panel included Francesca Spidalieri, Pell Center Senior Fellow for Cyber Leadership; Maurice Uenuma, Senior Vice President at Center for Internet Security; Geoff Hancock, CEO for the Advanced Cybersecurity Group; and Jack Nicholas, Director and General Counsel at Creative Services Inc.
The panel focused on the human element of cybersecurity and the recognition that every employee plays a part in securing the data, systems, and digital infrastructure of any organization. While frequently considered a technology-focused challenge, cybersecurity remains a profoundly human-centric endeavor. As IT professionals, humans are the ones who design, build, implement, maintain, and govern the systems which form the “central nervous system” of modern organizations. And humans, as employees of the organization, remain the most frequent avenue of cyber attack and constitute a major ongoing vulnerability to organizations everywhere. And it is humans, as nefarious actors, who conduct cyber attacks for a variety of (very human) motives. And humans, as cybersecurity professionals, are the ones who must identify, protect, detect, respond, and recover from cyber attacks.
Due to the deep human involvement in cybersecurity matters, proper workforce management is essential to enterprise resilience in the face of persistent cyber threats. This requires a holistic approach covering everyone from executives to front-line employees, from cybersecurity professionals to IT managers, and including the hiring, deployment, and management of the workforce. In turn, workforce management must be aligned to prioritized enterprise action.
 Mr. Uenuma and Mr. Hancock shared with the group gathered for the event some of the main highlights from the “Cybersecurity Workforce Handbook: A Practical Guide to Managing Your Workforce”, recently published by the Council on CyberSecurity (now integrated with the Center for Internet Security). The key topics covered during their respective presentations included: ways to align the workforce to prioritized action, assign essential tasks for the entire workforce, deploying mission-critical cybersecurity roles, building a security-oriented culture, and providing effective governance of cybersecurity activities. “In order to tackle the extent of cybersecurity threats we see in today’s world, a comprehensive approach needs to be utilized that spans across policy, technology, and people,” Mr. Uenuma stated.
Mr. Uenuma and Mr. Hancock shared with the group gathered for the event some of the main highlights from the “Cybersecurity Workforce Handbook: A Practical Guide to Managing Your Workforce”, recently published by the Council on CyberSecurity (now integrated with the Center for Internet Security). The key topics covered during their respective presentations included: ways to align the workforce to prioritized action, assign essential tasks for the entire workforce, deploying mission-critical cybersecurity roles, building a security-oriented culture, and providing effective governance of cybersecurity activities. “In order to tackle the extent of cybersecurity threats we see in today’s world, a comprehensive approach needs to be utilized that spans across policy, technology, and people,” Mr. Uenuma stated.  “Critically important in this process is equipping those individuals who are responsible for managing information systems, hiring cybersecurity talent, developing corporate policy and creating corporate culture. The Handbook is an asset to those individuals—providing guidelines for effective workforce management in the cybersecurity sphere.” As the Handbook points out, “there is a near-infinite list of ‘good things’ for every enterprise to do and to know to improve the security of cyberspace, but it’s seldom clear what to prioritize. This overload of defensive support if a ‘Fog of More’—more options, more tools, more knowledge, more advice, and more requirements… but not always more security. What is needed is a way to organize and prioritize activity around a set of actions known to be effective in addressing most threats.”
“Critically important in this process is equipping those individuals who are responsible for managing information systems, hiring cybersecurity talent, developing corporate policy and creating corporate culture. The Handbook is an asset to those individuals—providing guidelines for effective workforce management in the cybersecurity sphere.” As the Handbook points out, “there is a near-infinite list of ‘good things’ for every enterprise to do and to know to improve the security of cyberspace, but it’s seldom clear what to prioritize. This overload of defensive support if a ‘Fog of More’—more options, more tools, more knowledge, more advice, and more requirements… but not always more security. What is needed is a way to organize and prioritize activity around a set of actions known to be effective in addressing most threats.”
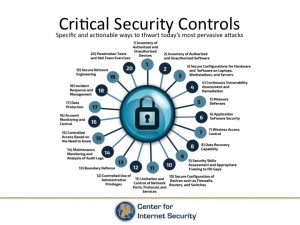 “We want to make best practices common practices,” Mr. Uenuma emphasized. Indeed, the list of Critical Security Controls for Effective Cyber Defense—specific and actionable ways to prevent and mitigate the most pervasive cyber attacks—represent the foundation of the Handbook.
“We want to make best practices common practices,” Mr. Uenuma emphasized. Indeed, the list of Critical Security Controls for Effective Cyber Defense—specific and actionable ways to prevent and mitigate the most pervasive cyber attacks—represent the foundation of the Handbook.
Mr. Hancock discussed the shortage of cybersecurity professionals and the need to optimize workforce planning to prioritize what is most important to each specific company and to get “the right people to do the right things.”  When asked who he would hire if he could add one more person to his hypothetical company, he quickly responded that he would look for a risk manager—not an IT expert, but somebody who understands enterprise risk and knows how to integrate business into security and security into business.
When asked who he would hire if he could add one more person to his hypothetical company, he quickly responded that he would look for a risk manager—not an IT expert, but somebody who understands enterprise risk and knows how to integrate business into security and security into business.
Ms. Spidalieri contributed insights and recommendations to the Handbook, especially with regard to the increasing role that non-technical executives and board members must play in their organizations’ overall cybersecurity posture and the need for them to see cyber risk as an integral component of their enterprise risk management process. She argues that “achieving cybersecurity is more than just a technical problem […] it is an operational issue that requires senior leaders to develop and implement overarching strategies that integrate best practices across policy, technology, and people.”
 Mr. Nichols shared his personal experience advising companies with state and federal laws in regards to hiring, retention, and privacy right within the workforce, and shared common challenges when trying to balance the need for more or new technology with what a small or medium-sized enterprise can afford. “The goal of every company is to make money, and the cost of ‘doing cybersecurity’ is often seen as just one more expense. But we just cannot afford not to do cybersecurity! The Handbook can help us prioritize tasks and strengthen our security best practices.”
Mr. Nichols shared his personal experience advising companies with state and federal laws in regards to hiring, retention, and privacy right within the workforce, and shared common challenges when trying to balance the need for more or new technology with what a small or medium-sized enterprise can afford. “The goal of every company is to make money, and the cost of ‘doing cybersecurity’ is often seen as just one more expense. But we just cannot afford not to do cybersecurity! The Handbook can help us prioritize tasks and strengthen our security best practices.”
To download a copy of the Cybersecurity Workforce Handbook, click here.
For more information on the Pell Center cybersecurity initiative and future events, visit the RICCI webpage or contact the Pell Center at [email protected].
The Rhode Island Corporate Cybersecurity Initiative is supported by The Verizon Foundation for the 2014-2015 academic year.

